前言
找了大堆资料,终于搞定CS的部署了,在这里分享给大家,后面还有CS的具体使用等。
PS:文章仅供学习使用,不做任何非法用途,后果自负!
一、CobaltStrike 4.0安装部署
1.传送飞机:
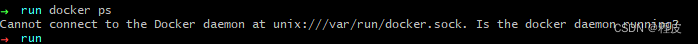
Cobalt Strike安装包请关注公众号,回复“**CS安装包**”即可获取。 2.这里将下载的安装包放在Kali当中,执行teamserver文件,即可安装启动cs服务端
./teamserver 172.16.XXX.XXX(kali的IP) 123456(密码随便设) 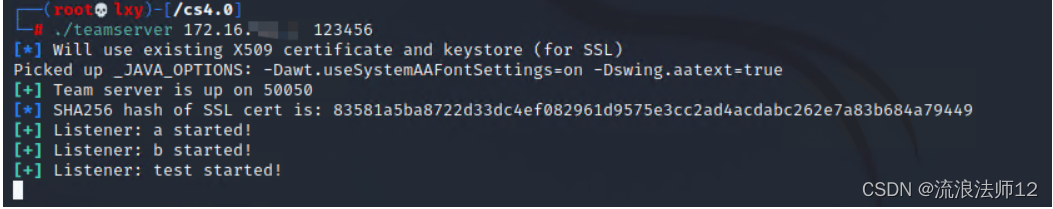
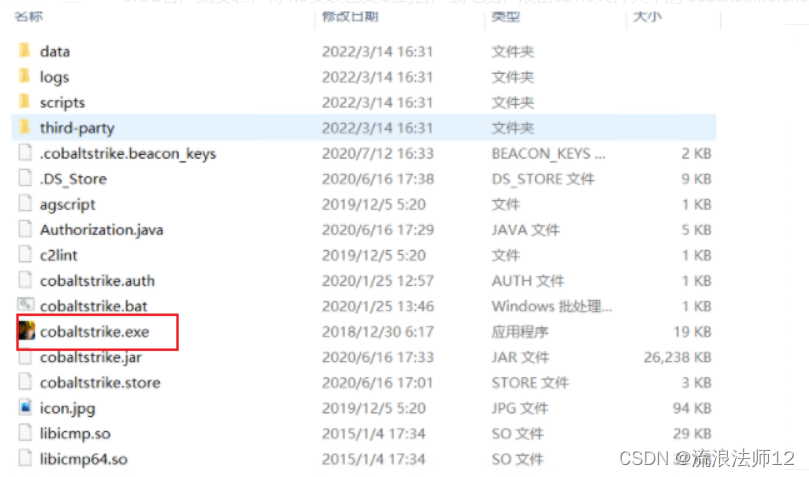
3.CS客户端安装,将4.0安装包复制到客户端电脑,双击cs4.0文件夹中的 cobaltstrike.exe 即可成功启动CS;
4.登录使用
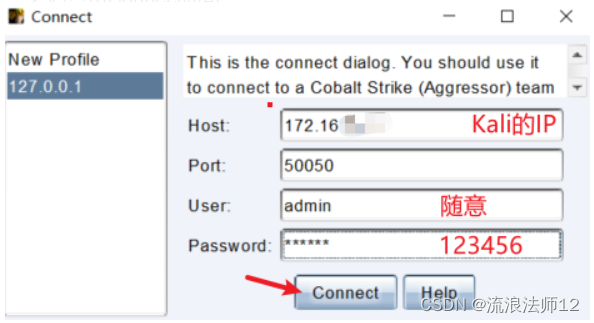
host:cs服务端地址 port:端口默认不变 user:用户名随便写 Password:123(服务端启动时输入的密码) 之后点击Connect即可 5.登录成功
二、Cobalt Strike 菜单介绍
1、Cobalt Strike
New Connection Preferences Visualization VPN Interfaces Listenrs script Manager close 2、View
Applications Credentials Downloads Event Log Keystrokes Proxy Pivots Screenshots Script Console Targets Web Log 3、Attacks
Packages: HTML Application MS Office Macro Payload Generator Windows Executable Windows Executable(S) Web Drive-by: Manage Clone Site Host File Scripted Web Delivery Signed Applet Attack Smart Applet Attack System Profiler Spear Phish #鱼叉钓鱼邮件
4、Reporting
Activity Report Hosts Report Indicators of Compromise Sessions Report Social Engineering Report Tactics, Techniques, and Procedures Reset Data Export Data 5、Help
Homepage Support Arsenal System information About 更多安全分享,请关注【安全info】微信公众号!
原文链接:https://blog.csdn.net/WEARE001/article/details/123494146?ops_request_misc=%257B%2522request%255Fid%2522%253A%252253208ae77c69f257655fc019b64bb6ec%2522%252C%2522scm%2522%253A%252220140713.130102334.pc%255Fblog.%2522%257D&request_id=53208ae77c69f257655fc019b64bb6ec&biz_id=0&utm_medium=distribute.pc_search_result.none-task-blog-2~blog~first_rank_ecpm_v1~times_rank-12-123494146-null-null.nonecase&utm_term=%E7%BE%A4%E6%99%96%E9%83%A8%E7%BD%B2